|
|
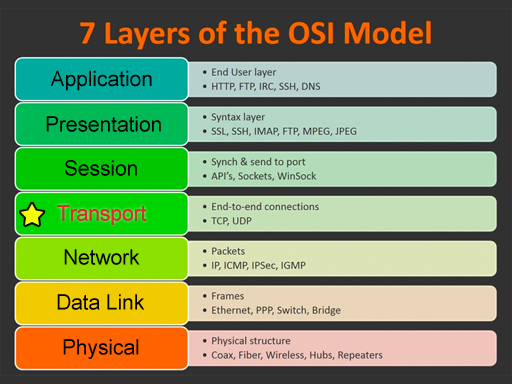
| This glossary uses network terms from the OSI model. Click on one of the categories on the left or on the image below. Click the View All link to see all terms. Use the alphabet to jump to that letter. Some of the terms could be used on multiple layers, but they are grouped in the most common layer. |
Transport
View All
|
|
|
#
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
|
A
ARP (Address Resolution Protocol) |
| The protocol responsible for associating a logical address (often from a Layer-3 protocol) with a physical address (often from a Layer-2 protocol). ARP is most often employed to broadcast a request on the local IP subnet for the Ethernet MAC (Media Access Control) address of a specific host when its corresponding IP address is already known. (Transport Layer) Top |
|
|
B
BGP (Border Gateway Protocol) |
| The exterior gateway routing protocol used to build the routing table of the commercial internet. BGP version 4 (BGP4) is the only exterior gateway protocol (EGP) in use today. Internet service providers (ISPs) use BGP to share external routes they learn from customers and other ISPs with one another. Propagating all routes among the ISPs of the internet enables all internet clients to access much of the internet’s sites and resources. (Transport Layer) Top |
|
|
Buffer |
| A digital memory location used to reduce the loss of data or the variation in the rate of data transmission. Without data buffers, a receiving system must be prepared to process external data presented to its interfaces immediately. Buffers are instrumental in communications systems in which variations in delay, known as jitter, can adversely impact the quality or usability of the system. Without such a buffer, real-time traffic must be compressed, or the transmission system must have no perceivable delay. (Transport Layer) Top |
|
|
F
FTP (File Transfer Protocol) |
| A TCP/IP protocol for transferring data between a client and server at the file level. FTP uses a pair of TCP ports, 20 and 21, in its insecure form and 989 and 990 with implicit security; the higher numbered port in each case is used to create, maintain, and then tear down the session while the lower one is used for the transfer of data. The term FTP is also often used loosely to refer to a utility that uses the FTP protocol in the background while presenting a graphical user interface (GUI) that resembles two folders—a local one and one representing the remote server folder—that allows files and folders to be dragged back and forth between them. (Transport Layer) Top |
|
|
M
Multiplexing |
| The combining of multiple sources of data traffic onto a single communications pathway. Multiplexing is also used to describe the process of interleaving the traffic of all transmitting or receiving applications across the same bitstream down through the protocol stack and across the network media. (Transport Layer) Top |
|
|
O
OSPF (Open Shortest Path First) |
| A link-state routing protocol that supports large private internetworks. OSPF is ideal for large enterprise networks when it is deployed as intended by establishing hierarchically addressed regions known as areas. (Transport Layer) Top |
|
|
P
Port |
| A physical interface on an electronic device; a differentiating logical identifier for an application or process. When used to refer to logical software identifiers, the term port often appears in discussions of the TCP/IP Transport-layer protocols TCP and UDP. Both protocols dedicate the first two fields in their headers to the source and destination numeric identifiers of the processes that they encapsulate. Common port numbers should eventually be recognized by network and security professionals because they are used in the configuration of firewalls and end devices to specify which processes should be allowed or denied access beyond the point of configuration. (Transport Layer) Top |
|
|
Protocol |
| An agreed upon method for communication; a set of rules for communication. Data protocols serve to standardize how endpoints and intermediate devices interoperate. Without one or more common protocols, two end devices fail to be able to communicate with one another. (Transport Layer) Top |
|
|
Public key cryptography |
| The use of a related public and private pair of cryptographic keys for authentication, confidentiality, or both. When the keys are generated along with a certificate by a trusted certificate authority (CA), their use is said to be a part of a public key infrastructure (PKI). PKI all but eliminates the possibility of a third party’s compromising the private key. The basis for the cryptography is that neither key can decrypt what it has encrypted. It takes the opposing key to do so. (Transport Layer) Top |
|
|
T
TCP (Transmission Control Protocol) |
| The primary Layer-4 protocol in the TCP/IP protocol suite. Along with UDP, TCP is one of two transport protocols responsible for carrying the traffic from higher-layer sessions across an internetwork. TCP is considered a reliable, connection-oriented protocol because a virtual circuit must be negotiated and established before data will begin to flow between the connection endpoints (connection-orientation) and because TCP acknowledges receipt of data (reliability). (Transport Layer) Top |
|
|
TCP/IP (Transmission Control Protocol/Internet Protocol) |
| The principal protocol suite in use in the industry today. TCP/IP is the protocol suite used on the internet. The suite consists of easily thousands of individual protocols, of which TCP and IP are only two but the most prominent two. As a protocol model, TCP/IP comprises four distinct layers, three fewer than the OSI Model because TCP/IP specifies application protocols that perform the tasks of the top three layers of the OSI Model, and the bottom two layers of the OSI model are not in the purview of TCP/IP but are relegated instead to the network adapter, such as an Ethernet NIC. (Transport Layer) Top |
|
|
U
UDP (User Datagram Protocol) |
| Along with TCP, one of the two Layer-4 transport protocols in the TCP/IP suite. UDP is an unreliable, connectionless protocol in that it offers best-effort delivery with no guarantees of arrival or flow control. (Transport Layer) Top |
|
|
V
Voice over Internet Protocol (VoIP) |
| A framework of protocols that enables two or more IP hosts, usually IP phones, to digitize and packetize analog voice signals and transmit them to one another. VoIP implementations use call setup protocols for a voice gateway (voice-enabled router) to signal to a gateway controller (a server) that one party would like to call another. (Transport Layer) Top |
|
|